Authentication Is Used for Which of the Following Purposes
It is common for authentication to use physical characteristics such as fingerprints secret knowledge such as passwords and security tools such as smart. Authentication is used in computer security and user access management systems.
User authentication can be as simple as requiring a user to type a unique identifier such as a user ID along with a password to access a system.

. This is part of the 8021 group of IEEE protocols. The Java TM Authentication and Authorization Service JAAS was introduced as an optional package to the Java TM 2 SDK Standard Edition J2SDK v 13. There are a number of authentication methods that can be used to confirm the identity of users who connect to.
The ANSI-41 authentication features are independent of the air-interface protocol used to access the network and subscribers are never involved in the process. In the Authentication Method section select the type of authentication that you want to use from among the following. It might involve validating personal identity documents verifying the authenticity of a website with a digital certificate determining the age of an.
By no means do authentication methods further encrypt your data. It is used only to authenticate clients and services used by them. While its unarguable that authentication methods minimize a users risk of identity theft its also unarguable they come with a fleet of flaws.
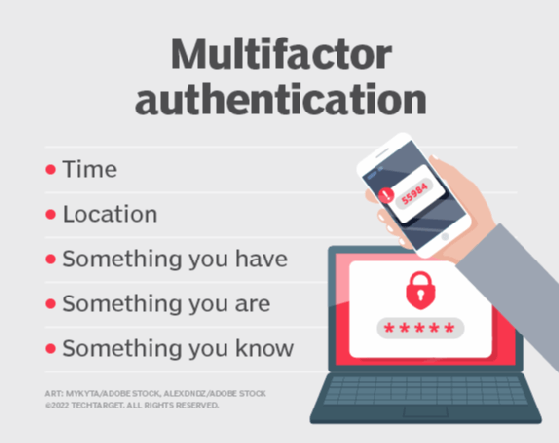
Choose three Select one or more. Something you know such as a password Something you have such as a smart card Something you are such as a fingerprint or other biometric method Identification occurs when a user professes an identity such as with a username and authentication occurs when users prove their identity. What you know Something you know such as a password PIN personal information like mothers maiden name etc.
Users have to prove they are who they say they are. It is the mechanism of associating an incoming request with a set of identifying credentials. The authentication key is shared much efficiently than public sharing.
The authentication process is divided into various types based on its process. For authentication of users to reliably and securely determine who is currently executing Java. Authentication is the process of verifying who a user claims to be.
Which of the following BEST describes the purpose of authentication. For authorization of users to ensure they have the access control rights permissions required to do the actions performed. Without the key third parties will be unable to view your data.
Authentication Authorization and Accounting AAA is an architectural framework to gain access to computer resources enforcing policies auditing usage to provide essential information required for billing of services and other processes essential for network management and security. Authentication is the process of recognizing a users identity. Not to be confused with the step it precedesauthorizationauthentication is purely the means of confirming digital.
Encryption protects data by scrambling it with a randomly generated passcode called an encryption key. Authentication provides identification to a resource and corrects when. 221 The forms of authentication are something you know have or are.
8021X should not be confused with 80211x which is an informal term used to denote any of the 80211 standards including 80211b 80211g and 80211n. A successful outcome of authentication occurs when it can be shown that the MS and the network possess identical results of a calculation performed in both the MS and the network. Authentication provides authorization in a resource and corrects when authenticated C.
It shows vulnerability to soft or weak passwords. Understanding Encryption and Authentication. 8021X permits or denies access to resources through the use of ports.
It can also be more complex however -- for example requiring a user to provide. Retinal scans are considered something you are. There are three factors of authentication.
LDAP refers to Lightweight Directory Access Protocol. JAAS has now been integrated into the J2SDK v 14. It implements port-based Network Access Control or PNAC.
Authentication provides logging to a resource and corrects when authenticated B. However hackers can attempt to steal access by impersonating an authorized user. Computer Science questions and answers.
Authentication Methods Used for Network Security. Single-use cards such as this are called common access cards CACs. 1st - Client requests authentication.
JAAS can be used for two purposes. Computer and User using Kerberos. Some disadvantages of Kerberos.
What you have A physical item you have such as a cell phone or a card. This process is mainly used so that network and software. Selecting this option tells the computer to use the authentication method currently defined by the local administrator in Windows Defender Firewall or by Group Policy as the default.
There are three common factors used for authentication. In contrast with identification the act of indicating a person or things identity authentication is the process of verifying that identity. The credentials provided are compared to those on a file in a database of the authorized users information on a local operating system or within an authentication server.
While just one facet of cybersecurity authentication is the first line of defense. Lightweight Directory Access Protocol LDAP. For authentication of users to reliably and securely determine who is currently executing Java code regardless of whether the code is running as an application an applet a bean or a servlet.
Authentication methods simply add rigor to your sign-in process. It is the process of determining whether a user is who they say they are. Smartcard authentication relates to something you have and something you know the PIN.
It provides support for data integrity and authentication of IP data packets. This identification process verifies a users identity usually through something they know such as a password something they have such as an ID card or USB token or something they are via biometrics. The user inputs his password and the system hashes the combination of the password and challenge together using a one-way hash function.
81 of security incidents were tied to stolen or weak passwords in 2018. Encryption authentication helps protect the key. How is authentication used.
Personal identification verification cards are used to control user access to resources such as buildings and computer systems. For the purpose of authentication what three methods are used to verify identity. For authentication of users to reliably and securely determine who is currently executing Java code regardless of whether the code is running as an application an applet a bean or a servlet.
Something you do something you are something you have something you know where you are Refer to curriculum topic. Users have to prove theyre allowed to do what they are trying to do. Authentication enables the user or computer system to authenticate the user to the application at the other end and based on the results it decides whether to allow or reject the user.
2nd - authentication server sends a challenge message to the user or host. JAAS can be used for two purposes. Authentication is the act of proving an assertion such as the identity of a computer system user.
It is a fundamental component of information security that essentially validates that entities are who or what they claim to be. Authentication is the process of verifying the identity of a person or digital entity.

Applications Of One Time Password Otp One Time Password Unified Communications Otp

Aws Ec2 General Purpose Instance Properties Network Performance Machine Learning Learning Resources

Comments
Post a Comment